IT Assurance & consulting
Why Mazars?
We believe we are an excellent fit to provide IT assurance and cyber security services to Qatari companies for the following reasons:
Expertise
We have been providing cyber security and IT security services as part of a number of consulting and internal audit (both outsourced and co-sourced) engagements to a significant number of financial, manufacturing and distribution companies.
The team is composed of individuals carrying the most recognised information security certifications such as CISSP, GPEN, CEH, CISA, CISM, CRISC, ITIL, ISO 27001 lead auditor, CE, CE+ and IASME Gold assessors.
Leadership by a strong partner-led team
This is where we really excel. We genuinely provide a partner-led team with partners ‘on the ground’ giving you the best senior input and added value recommendations at a cost which is extremely competitive. This level of senior input is unique amongst firms who provide internal audit services, as demonstrated by your central point of contact.
Rigorous standard based approach
We employ various standards and framework such as ISO 27001, NIST 800 series and SANS/CPMI critical controls. In addition we would refer to ISACA (COBIT) and Prince 2 (project management) for specific matters. As members of the ISACA and certified cyber security assessors, these standards form a core part of our methodology. We understand how to apply these standards in practice rather than just in theory.
Meeting your requirements (client centric)
We are confident that Mazars develop cyber security solution that is customised to meet our clients requirements for a trusted and highly skilled cyber security review and penetration testing. This is demonstrated within this document.
Credibility
As a leading global audit and consulting firm, we are a credible partner to Qatari companies and a recognised and trusted audit brand internationally. We act as auditors/ advisors to over 15% of European companies and to over 400 companies listed on 20 different stock exchanges internationally.
Our partner-led team has the right combination of skills, experience and credibility required to satisfy your cyber security review needs. The team has built up a strong reputation in the marketplace for the delivery of cyber security services, built upon its breadth and depth of specialist knowledge and experience.
Independence and objectivity
Should Mazars be appointed to provide cyber security review services for Qatari companies, we do not anticipate any conflicts of interests which would compromise our ability to deliver our services with on-going independence and objectivity. None of our partners or staff members sit on the Boards of, or are employed by, any of the organisations we are engaged with and we act independently for each of our clients. We would manage any potential conflicts of interest in line with our standard practices.
OUR METHODOLOGY
Methodology
Mazars proposes several cyber security assessment options that cover a broad risk spectrum. These assessments and their coverage are presented here.
Mazars has a global methodology for performing cyber security reviews. Our methodology is a risk based approach focusing on clients’ strategic objectives and the risks and uncertainties which may affect their ability to achieve them. Our approach is based on globally recognised standards, guidelines and framework such as ISO 27001, NIST 800 series and SANS/CPMI.
Cyber Security Assessment
Our assessment offers a level of assurance around five areas:
- Firewalls and internet gateways: Enumeration of external network, identification of running services and vulnerabilities and ensure firewall is secure.
- Secure configuration: Assess internal host, identify running services and vulnerabilities.
- Access control: Existence of generic accounts, end-users with privileged access, password protection
- Malware protection: Malware injection through emails or from electronic media (USB sticks)
- Patch management: Patch installation against baseline (vendor patch list).
Part of these tests will be run using internationally recognised tools such as Nessus scanner, nmap, MBSA, Burp Suite, OWASP WAP or Titania.
Advanced Cyber Security Assessment
Full assessment will complement the Cyber Security Assessment five domains with:
- Risk management
- Governance (Information Security)
- Training (security awareness)
- Policies & Procedures
- Security Incident management
- Business continuity aspects
Cyber security control categories
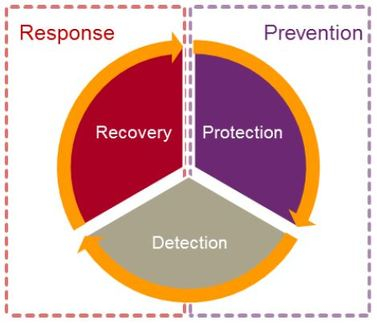
There are three main categories of activities needed to respond to cyber threats.
There is a common set of factors to be considered when assessing the effectiveness of an organizations business, which are summarized below. These are much the same as those for cyber security, which is most cost effective when considered to be part of the business.
Protection
| Detection
Recovery
|
